Greetings and salutations fellow readers.
Recently I’ve had to step into the awful world of kernel debugging. When malware drops a rootkit and conventional userland debugging falls short, you have to step into ring 0. Unfortunately, options are rather limited when it comes to decent ring0 debugging on windows.
What’s that one debugger everyone’s heard of but can’t ever get working? If you said SoftIce, you’re right. Getting softice to run these day’s is a pain in the butt. Especially since its largely broken in Windows 7, support ended in 2006, and the damn thing crashes even if you do get it working. There has got to be SOME alternative right?
Enter Syser. SoftIce 2 – Electric Boogaloo.

There are a few things Syser does that Softice don’t –
1) Colors
2) More than 1 CPU
3) Source debugging
4) Windows 7/8
5) A better looking GUI
At this time however, the website that hosts Syser is offline. This makes obtaining it harder than usual, but not impossible. I think CNET offers a download.
Can you run Syser in a VM? Of course!
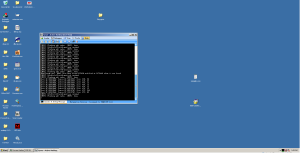
But that doesn’t mean there aren’t a few things you need to do to get shit working right.
Problems I ran into on VirtualBox:
-
Screen refresh
Mouse Not Working
Random BSODs
-=Screen Refresh=-
If you can somehow modify the source for VirtualBox, adjust the screen refresh rate to be every 5 seconds or so.
My way around this in VirtualBox is to run windows in 256 color mode. It looks ugly as sin, but it works fine at any resolution.
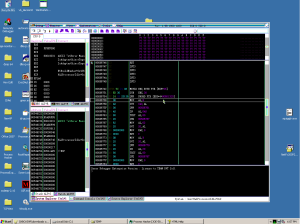
The alternative to that is clicking outside the window every second. That said, a way to force a refresh would be some sort of app with a time that constantly calls ‘UpdateWindow’. I was thinking something like this:
#include <windows.h> VOID CALLBACK TimerProc(HWND hWnd, UINT nMsg, UINT nIDEvent, DWORD dwTime) { HWND mywind = FindWindow(NULL,"xp crapbox"); // name in window title UpdateWindow(mywind); } int main(int argc, char *argv[]) { MSG Msg; UINT TimerId = SetTimer(NULL, 0, 5000, &TimerProc); // 5 seconds if (!TimerId) return 16; while (GetMessage(&Msg, NULL, 0, 0)) { DispatchMessage(&Msg); } KillTimer(NULL, TimerId); // app exit cleanup return 0; }
It beats compiling VirtualBox from source just to adjust the refresh.
-=Mouse Not Working=-
The problem here is that Syser will not attempt to use your USB emulated mouse. It will instead load the driver for a PS/2 mouse (remember those?).
The fix is to set the pointing device to use PS/2 instead of USB.
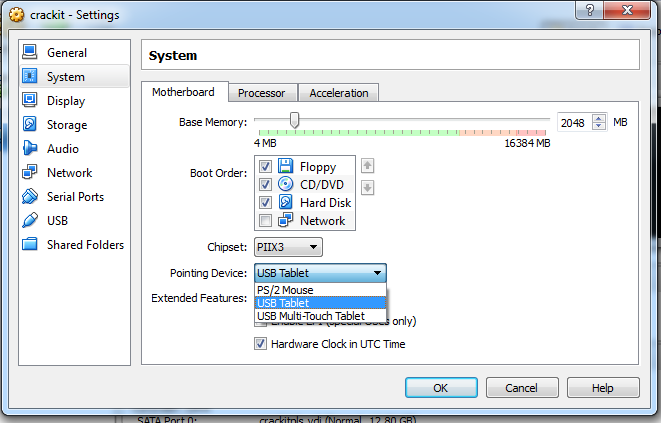
Also be sure to adjust the mouse sensitivity value in Syser’s config settings.
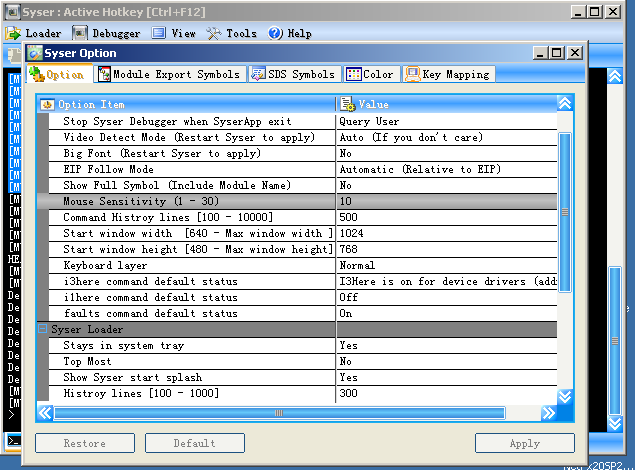
-=Random BSOD’s=-
Easy solution – snapshots. Kinda lame, but expect BSOD’s when working with a kernel debugger. It’s just a part of life.
Problems I ran into on VMWare:
“Unable to start MSI” – I cant even install the piece of shit. For all intents and purposes I’ll be focusing on getting syser working on VirtualBox. If you use vmware, add the following lines to your vmware config file:
vmmouse.present = “FALSE”
svga.maxFullscreenRefreshTick = “5”
This will allow you to make use of the mouse and be able to actually see the syser window without having to switch to the desktop and vm over and over. Or you could run my program from above and disregard the mouse.
-=Running Syser=-
Much like Softice, Syser has a keyboard shortcut to invoke the debugger and essentially ‘pause’ execution of the OS. Control + F12.
When paused like this, you can single step just like any other debugger. ‘F5’ will continue execution with Syser running. Pressing control + F12 will unload the Syser driver. F11 to step in, F10 to step over.
The command console (control + 2) allows for windbg style commands to be entered:
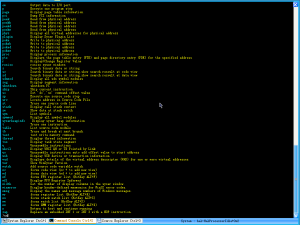 .
.
Quite powerful, but one might prefer to see what they’re doing and stick with the system explorer.
Opening processes for access is done via the command ‘addr’ (just like SoftIce) + the process ID in hex. Have a calculator handy.
If you have a rootkit or driver file and you want to inspect it, just type ‘load
This will allow you to run the driver on your own pace without waiting for it to be loaded externally:
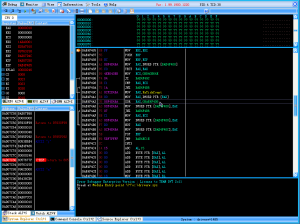
Anywho, I thought I’d share this awesome tool with you all before my next blog post in which I will be diving deep into the FinFisher malware dropped on WikiLeaks a few weeks back. I saw a writeup done, however it was incomplete after peeking through the malware myself. Except a nice entry / writeup on this malware soon.

